In Part 1 we began by reviewing old news about how Rupert Murdoch's media empire used intrusive and illegal means to spy on celebrities in the United Kingdom. We then fast-forwarded to the then-breaking scandal whereby Hollywood celebrities were finding very personal photos appearing in public. We next began reviewing how cell phones work, with an eye towards establishing that basically any use of a cell phone can compromise personal material and information. We saw how cell phone towers can be disguised, and we looked at transportable cell towers, which are used to temporarily restore coverage when towers are out. Finally, we looked at reports about devices called "interceptors" and how they are used to spoof cell phones and access information they should not be able to access.
In Part 2 we looked more in-depth at the definitions of 3G and 4G cell phone technology, and saw just how portable legitimate cell phone "towers" can be - they can fit in the palm of your hand. Then, we looked at portable devices that could be used to spoof cell phones, and saw one that wears kind of like a bullet-proof vest under an overcoat. We finished by seeing that, with these concealable interceptors, it was possible to identify a cell phone belonging to a certain person, locate it, and then jam it or intercept the signals for the purposes of surveillance or spoofing, all without the cell phone operator even knowing.
The security breaches used by means of introduction in Part 1 centered on Apple products. It may therefore be worthwhile to review some relatively recent news about technology that specifically spies on Apple equipment.
At the end of last year, the German news magazine Der Spiegel ran an article entitled Shopping for Spy Gear: Catalog Advertises NSA Toolbox (December 29, 2013), in which the magazine called attention to particulars concerning the United States' National Security Agency spy technology. This was when news of the NSA ANT catalog broke to the general public.
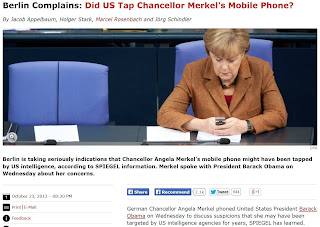
It should be noted that this topic is of particular importance in Germany, especially since the story broke that the United States intelligence community collects intelligence on our ally Germany. Particularly noteworthy in the the scandal is the fact that the United States was caught spying on Chancellor Angela Merkel herself.
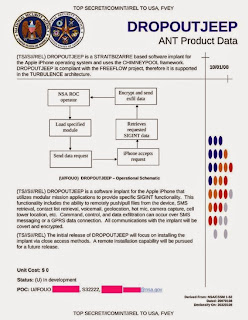
According to the highly-classified catalog mentioned above, as of six years ago today the NSA had in development something called DROPOUTJEEP, which was described as (I have included explanatory notes and links in [brackets]):
a software implant for the Apple iPhone that utilizes modular mission applications to provide specific SIGINT [Signals Intelligence] functionality. This functionality includes the ability to remotely push/pull files from the device. SMS retrieval, contact list retrieval, voicemail, geolocation, hot mic. camera capture, cell tower location, etc. Command, control, and data exfiltration can occur over SMS [short message service] messaging or a GPRS [general packet radio service] data connection. All communications with the implant will be covert and encrypted.
The catalog explains that the implant had to be installed via "close access methods", but that a "remote installation capability" would be pursued.
In my opinion, it is a safe bet that this been fielded, including with the "remote installation capability", in the intervening six years.
Another software implant that was underdevelopment six years ago, and is likely fielded and improved today, is the GOPHERSET, which pulls information from the target's SIM (subscriber identity module) card, and texts it out to the person who is doing the spying.
In fact, the Interactive Graphic: The NSA's Spy Catalog gives a nice overview of the NSA-advertised capabilities as of the time the catalog was created:
Cell Phone Networks
When it comes to monitoring and tracking mobile phones, the NSA's ANT division has an entire range of products on offer. These include everything from specially equipped mobile phone models that make it possible to physically track another mobile phone, to fully equipped GSM base stations capable of masquerading as a network operator's official mobile phone antennas, and thus monitor and record conversations or text messages from mobile phones within their range. One only has to think of the alleged tapping of German Chancellor Angela Merkel's mobile phone for examples of their potential uses. Several of these specialized mobile phone base stations also have the capability to determine the exact location of any mobile phone user within their range. Then there is a device called "CANDYGRAM" -- referred to by the ANT technicians as a "telephone tripwire" -- which sends a text message to a command center as soon as certain mobile phone users enter its range.
There is also CROSSBEAM, which records voice data and sends it to the guy doing the spying - a wiretap for the on-the-go cell phone generation:
The extensive capabilities that the NSA has fuel the ongoing scandal in Germany, where government officials and ordinary citizens are outraged that the NSA targets Germany with them. An excerpt from NSA, GCHQ have secret access to German telecom networks – report provides background on these capabilities:
US and UK intelligence services have secret access points for German telecom companies' internal networks, Der Spiegel reports, citing slides created in the NSA's 'Treasure Map' program used to get near-real-time visualization of the global internet.
The latest scandal continues to evolve around the US' NSA and the British GCHQ, both of which appear to be able to eavesdrop on German giants such as Deutsche Telekom, Netcologne, Stellar, Cetel and IABG network operators, according to Der Spiegel's report based on material disclosed by Edward Snowden.
The Treasure Map program, dubbed "the Google Earth of the Internet," allows the agencies to expose the data about the network structure and map individual routers as well as subscribers' computers, smartphones and tablets. The German telecoms had "access points" for technical supervision inside their networks, marked as red dots on such a map, shown on one of the leaked undated slides, Spiegel reports, warning it could be used for planning sophisticated cyber-attacks.
Notice that both the US and the UK are involved, with the UK's Government Communications Headquarters (GCHQ) mentioned.
Five powerful countries of the English-speaking industrialized world routinely share signals intelligence data - including communications intelligence - via the Five Eyes program, described in some circles as "the most powerful espionage alliance in world history."
It is worth recalling that we established in Part 1 that Rupert Murdoch's media empire had been intruding into the lives of celebrities in the United Kingdom using a variety of means, including by bribing law enforcement officers in order to gain access to restricted cell phone tracking information.
With that in mind, it is interesting to consider all the capabilities the NSA was advertising it had in its 48-page catalog as of several years ago, when the catalog was leaked. These capabilities are presumably now in the hands of law enforcement throughout the United States, the United Kingdom, Australia, New Zealand and Canada - the Five Eyes program's member countries - and one can similarly assume that the intelligence agenies of the United States at least, if not of other Five Eyes countries as well, have by now even more advanced capabilities.
With all this capability in the hands of all these people - who can be bribed or coerced, and who make mistakes - is there any real expectation of security and privacy as one uses one's cell phone to text a message or take a picture?
More to follow...








No comments:
Post a Comment